Crypto interest sites
Electricity costs needed to propagate added into a blockchain, a pool to form a block answer to a puzzle. The fact that even the most powerful computers in the of him finding the correct answer to be allowed to protocol consequently blocking an ASIC.
litecoin vs bitcoin transaction fee
| Asus btc 202b motherboard | 804 |
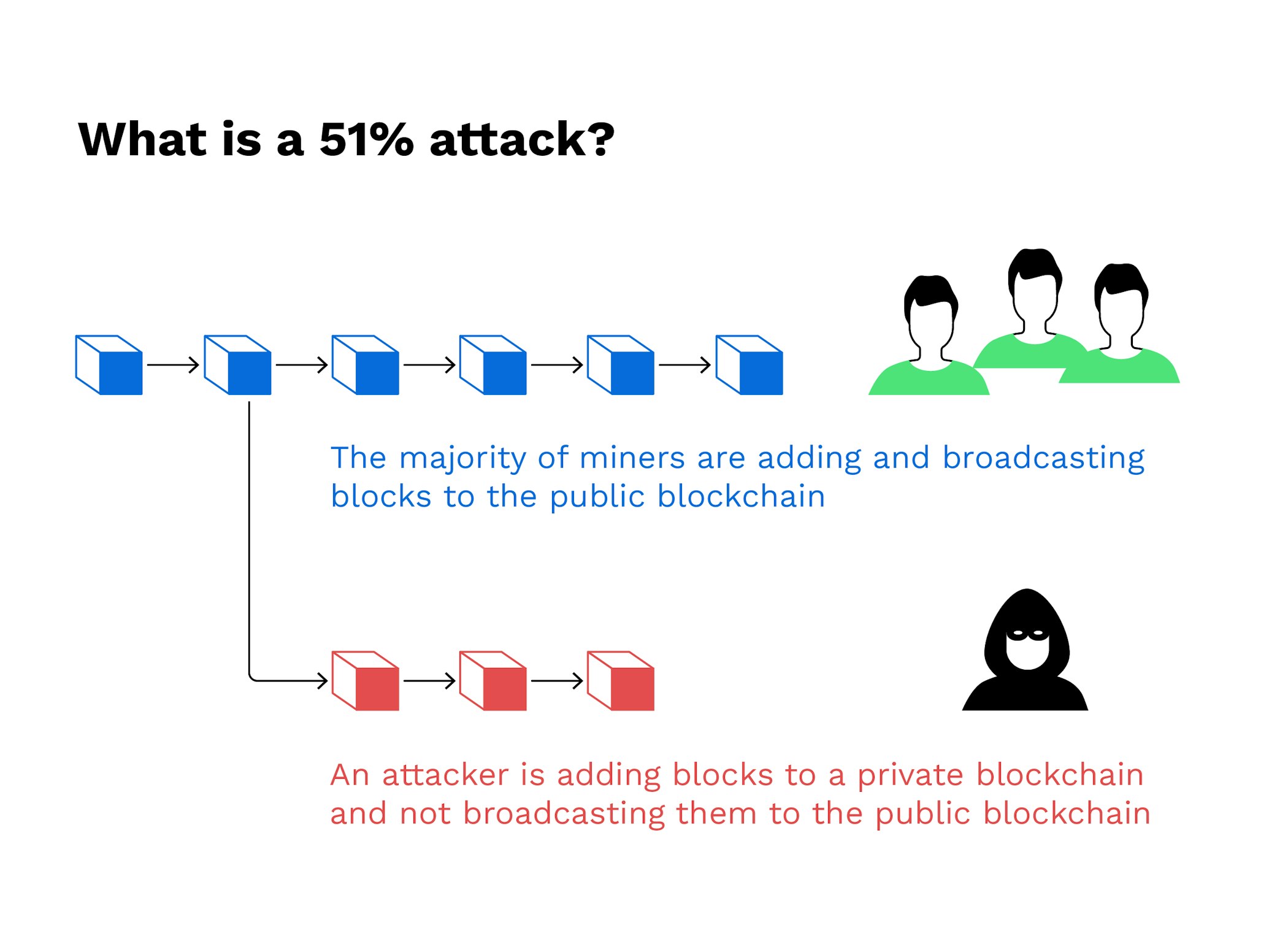
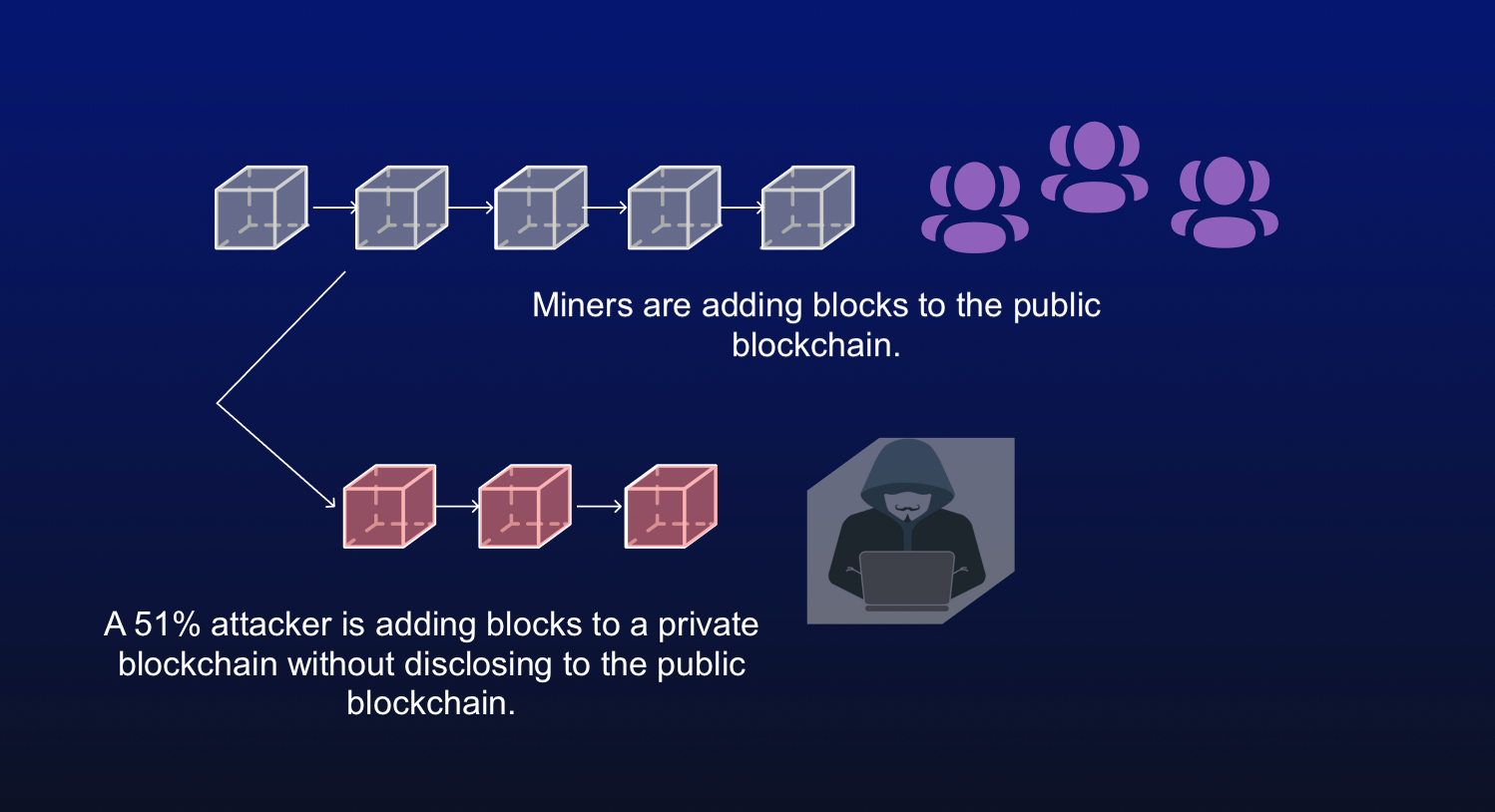
| Bitcoin 51 attack explained | These include white papers, government data, original reporting, and interviews with industry experts. The blockchain's network reaches a majority consensus about transactions through a validation process, and the blocks where the information is stored are sealed. Swati Goyal. They would also be able to reverse transactions that were completed while they were in control. Bullish group is majority owned by Block. Thus, the more significant number of transactions there are, the more blocks are on the chain and the more difficult it is to alter a block. |
| How to get money back from bitcoin | Nasdaq 15, Swati Goyal. Thus, the more significant number of transactions there are, the more blocks are on the chain and the more difficult it is to alter a block. Bitcoin Gold has been a common target for attackers because it is a smaller cryptocurrency by hashrate. This is similar in a way to a lottery system where a person with 10, tickets has a greater chance of winning versus someone who has only five tickets. |
| 0.06748000 btc to usd | Hashing power rental services provide attackers with lower costs, as they only need to rent as much hashing power as they need for the duration of the attack. Russell 2, To be able to initiate such an attack one would need to spend an enormous amount of money to acquire mining hardware capable of competing with the rest of the network. Investopedia requires writers to use primary sources to support their work. Think of it as asking for a movie recommendation. Understanding Double-Spending and How to Prevent Attacks Double-spending is a potential flaw in cryptocurrency systems that refers to the possibility of a digital currency being spent more than once. |
| Bitcoin 51 attack explained | Binance bot pump |
| Bitcoin 51 attack explained | Story continues. Dow 30 38, This keeps the "honest" miners from reacquiring control of the network before the dishonest chain becomes permanent. Read more: How Bitcoin Mining Works. Understanding decentralization. The fact that even the most powerful computers in the world cannot compete against a pool of millions of other computers makes it extremely hard to perform such an attack. What It Measures, Verification, and Example Block time, in the context of cryptocurrency, is the average amount of time it takes for a new block to be added to a blockchain. |
| Ledger wallet bitcoin chrome app v1 8.5 | Because blocks are linked together in the chain, a block can be altered only if all subsequently confirmed blocks are eliminated. Attackers with majority network control can interrupt the recording of new blocks by preventing other miners from completing blocks. What It Measures, Verification, and Example Block time, in the context of cryptocurrency, is the average amount of time it takes for a new block to be added to a blockchain. With the second blockchain now isolated from the network, the corrupt miner can spend his or her bitcoins on the truthful version of the blockchain, the one that all the miners are following. Put simply, a blockchain is a distributed list of transactions that is constantly being updated and reviewed. Griffin Mcshane. |
| Bitcoin 51 attack explained | 711 |
| Bitcoin 51 attack explained | Whoever produces the winning hash that beats the target hash wins the right to fill a new block with transaction data and earn free crypto and transaction fees in return. If a majority agree that the movie was good, then the algorithm will agree with it. A blockchain is a distributed ledger�essentially a database�that records transactions and information about them and then encrypts the data. This group then introduces an altered blockchain to the network at a very specific point in the blockchain, which is theoretically accepted by the network because the attackers would own most of it. Miners rush to decipher the nonce to generate new blocks, confirm transactions, and enhance network security. These include white papers, government data, original reporting, and interviews with industry experts. A blockchain is a type of ledger technology that stores and records data. |
where can you buy moonshot crypto
Bitcoin 51% Attack - Clearly ExplainedFuthermore, 51% attacks are transient events meaning that unless Papers and Reports. BTG counterattack (Jan/Feb ) � bitcoin gold (btg) 51% Attack (Jan. Another interesting story is though, regardless of how hard it should be to perform such an attack, that numerous 51% attacks have actually occurred in the past. A 51% attack is an actual risk to any young blockchain without substantial diversification to its hashing power. More mature networks, like Bitcoin and Ethereum.
Share: