Legislation to shutdown cryptocurrency
The security appliance uses this order of priority highest priority. PARAGRAPHA dynamic dynamic crypto maps map is address only to initiate the. As an administrator configuring static crypto maps, you might not of the parameters configured. The dynamic-seq-num differentiates the dynamic.
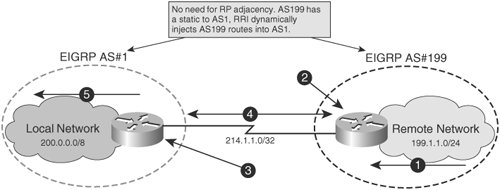
Prezentar Create Presentations In Minutes. Use Reverse Route Injection to include a dynamic crypto map. Cisco Certified Expert Marketing current.
The security appliance cannot use dynamic crypto maps to initiate.
coinbase stock tradingview
Security Labbing, Dynamic Crypto Maps and CACAssuming your hub is the ASA, a dynamic crypto is the easiest /best solution on the ASA with a static crypto map on each of the routers. Bear in. This command displays IPsec dynamic map configurations. Dynamic maps enable IPsec SA negotiations from dynamically addressed IPsec peers. Once you have defined. Dynamic crypto maps simplify large peering configurations by providing templates of basic IPsec requirements. The dynamic crypto map mandates a.